VMware ESXi 6.0 increased scalability by doubling almost all the numbers. Cluster size is now 64 hosts (previously 32) with up to 8000 VMs in single cluster. You can read all the details about scalability of vSphere 6 and VMware ESXi hypervisor in my detailed post here – vSphere 6 Features – New Config Maximums, Long Distance vMotion and FT for 4vCPUs. But in this post I’d like to point to changes to ESXi Security and all the enhancements that have been done concerning ESXi 6.0 Security and Password Complexity.
ESXi introduces new ESXCLI commands to manage local accounts. Those commands can add, list, modify or remove users across all hosts in a cluster through vCenter server. Functionality previously only available through direct connection to a host.
Permisson management can now also be done centrally – settings, removing, listing local permissions on ESXi servers.
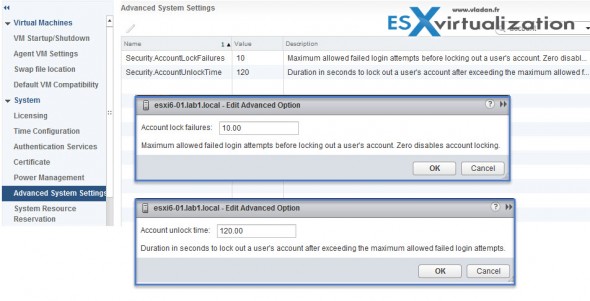
Account Lockout – new settings (two of them) which are in ESXi Host Advanced System Settings for the management of local account failed login attempts and account lockout duration. These parameters affect SSH and vSphere Web Services connections. The direct access to the console (DCUI) and console shell access are not affected..
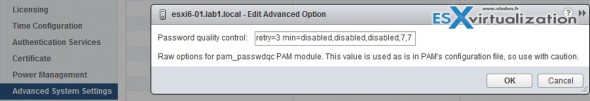
Password Complexity Rules – change here where In previous versions of ESXi, password complexity changes had to be made by hand-editing the /etc/pam.d/
passwd file on each ESXi host. In vSphere 6.0 now this can be done by adding an entry in Host Advanced System Settings, enabling centrally managed setting changes for all hosts in a cluster.
passwd file on each ESXi host. In vSphere 6.0 now this can be done by adding an entry in Host Advanced System Settings, enabling centrally managed setting changes for all hosts in a cluster.
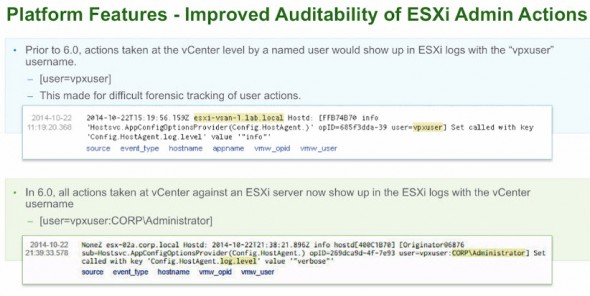
Improved Auditability of ESXi Administrator Actions – vSphere 5.x the logs showed “vpxuser” in the logs when actions were triggered in vCenter server. Now in vSphere 6.0, all actions at the vCenter Server level against an ESXi server appear in the ESXi logs with the vCenter Server username—for example, [user=vpxuser:DOMAIN\User].
Gives better details “who did what” on vCenter to execute actions on ESXi hosts….
Screenshot from VMware technical video overview of the ESXi 6.0 hypervisor…
New and More Flexible Lockdown Modes
Normal Lockdown Mode – The first mode. The DCUI access is not blocked so users on the “DCUI.Access” list are able to access DCUI.
Strict lockdown mode - In this mode, DCUI is stopped.
What is “exception users?”
These are local accounts or Microsoft Active Directory accounts with permissions defined locally on the host where these users have host access. You can define those exception locally on the host, but it’s not recommended for normal user accounts, but rather for service accounts. You should set permissions on these accounts to strict minimum and anly what’s required for the application to do its task and with an account that needs only read-only permissions to the ESXi host.
This is basically the same principle of local server accounts on Windows member server, where you can create local accounts, but as a best practice to give them only the permissions they need…
Smart Card Authentication to DCUI – There is new function, but apparently it is for U.S. federal customers only. It allows DCUI login access using a Common Access Card (CAC) and Personal Identity Verification (PIV). In this case the ESXi host must be part of Microsoft AD.
No comments:
Post a Comment